Control Summary
Establish and maintain a security awareness program to influence behavior among the workforce to be security conscious and properly skilled to reduce cybersecurity risks to the enterprise.
Why is it needed?
The behavior of individuals holds a pivotal role in determining the effectiveness or ineffectiveness of an enterprise’s security measures. It is notably simpler for an attacker to manipulate a user into clicking on a malicious link or opening an email attachment to introduce malware and gain unauthorised access to the enterprise, as opposed to seeking direct network exploits.
Users themselves, whether through deliberate actions or inadvertent mistakes, can precipitate security incidents. These incidents may stem from mishandling sensitive data, sending emails containing confidential information to unintended recipients, misplacing portable end-user devices, opting for weak passwords, or employing identical passwords across both sensitive and public platforms.
Implementing Control
Educates users about cyber safety in your business.
Implementation Group 1 requires the following eight safeguards:
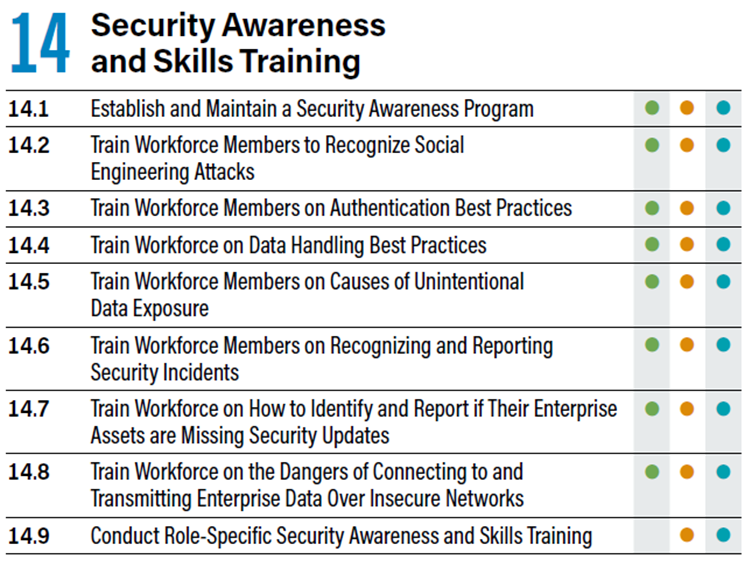
14.1 Establish and Maintain a Security Awareness Program
Making cybersecurity awareness training effective involves designing a program that is topical and relevant to your environment. Cybersafety messages should be dispersed regularly to ensure they remain targeted, relevant and front of mind.
14.2 Train Workforce Members to Recognise Social Engineering Attacks
Provide training for employees to identify social engineering tactics, including phishing, pretexting, and tailgating.
14.3 Train Workforce Members on Authentication Best Practices
Additional essential safeguards are training users on best practice authentication (Multi-factor Authentication and safe password use), secure data handling and the causes of unintentional data exposure, and the risks of connecting to and transferring data over insecure networks.
14.4 Train Workforce on Data Handling Best Practices
Educate employees on the proper identification, storage, transfer, archiving, and disposal of sensitive data. Additionally, provide training on best practices for maintaining clear screens and desks, such as securing screens when leaving their enterprise assets unattended, erasing physical and virtual whiteboards after meetings, and ensuring the secure storage of data and assets.
14.5 Train Workforce Members on Causes of Unintentional Data Exposure
Educate employees on recognising the reasons behind unintentional data exposure. Topics to cover include mishandling sensitive data during delivery, misplacing portable end-user devices, and inadvertently sharing data with unintended recipients.
14.6 Train Workforce Members on Recognizing and Reporting Security Incidents
Train employees to both identify potential incidents and report them effectively.
14.7 Train Workforce on How to Identify and Report if Their Enterprise Assets are Missing Security Updates
Provide training to the workforce to ensure they can proficiently verify and report instances of outdated software patches or failures in automated processes and tools. This training should also encompass the importance of promptly notifying IT personnel about any issues with automated processes and tools.
14.8 Train Workforce on the Dangers of Connecting to and Transmitting Enterprise Data Over Insecure Networks
Educate workforce members about the risks associated with connecting to and transmitting data over insecure networks for enterprise activities. When dealing with remote workers, the training should also emphasise the importance of securely configuring their home network infrastructure to safeguard the enterprise’s data.
Additional safeguards at level 2 or 3:
14.9 Conduct Role-Specific Security Awareness and Skills Training
