Control Summary
Establish and maintain data recovery practices sufficient to restore in-scope enterprise assets to a pre-incident and trusted state.
Why is it needed?
Within the cybersecurity triad, consisting of Confidentiality, Integrity, and Availability (CIA), there are scenarios where the availability of data holds greater significance than its confidentiality. Enterprises rely on a multitude of data types for informed decision-making, and any absence or lack of trustworthiness in that data can potentially impact the enterprise’s operations. A straightforward example of this can be observed in the context of a transportation enterprise’s reliance on accurate weather information.
When attackers infiltrate assets, they enact various changes to configurations, introduce new accounts, and frequently install software or scripts. Detecting these alterations can be challenging, as attackers might have manipulated or replaced trusted applications with malicious variants, or the modifications may resemble ordinary account names. Configuration adjustments can involve the addition or modification of registry entries, the opening of ports, the disabling of security services, the deletion of logs, or other actions that compromise system security. It’s worth noting that these actions are not necessarily malicious in nature; they can also result from human errors. Therefore, it is imperative to maintain recent backups or mirrors to facilitate the restoration of enterprise assets and data to a verified, trusted state when needed.
Implementing Control
The basic level of this control involves establishing and maintaining a data recovery process. The scope of recovery efforts should be defined along with recovery prioritisation and the security requirements for all backup data.
Implementation Group 1 requires the following four safeguards:
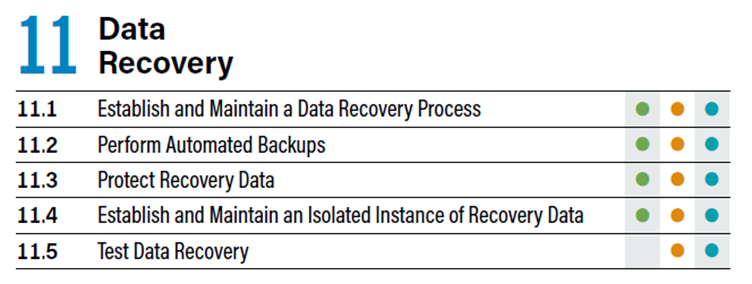
11.1 Establish and Maintain a Data Recovery Process
The scope of recovery efforts should be defined along with recovery prioritisation and the security requirements for all backup data.
11.2 Perform Automated Backups
Backups should be automated for all in-scope assets and run at least weekly.
11.3 Protect Recovery Data
Data in backups must be protected with equivalent security mechanisms as the primary data using tools such as encryption and data separation.
11.4 Establish and Maintain an Isolated Instance of Recovery Data
Isolated instance of all recovery data should be established and maintained.
Additional safeguards at level 2 or 3:
11.5 Test Data Recovery
